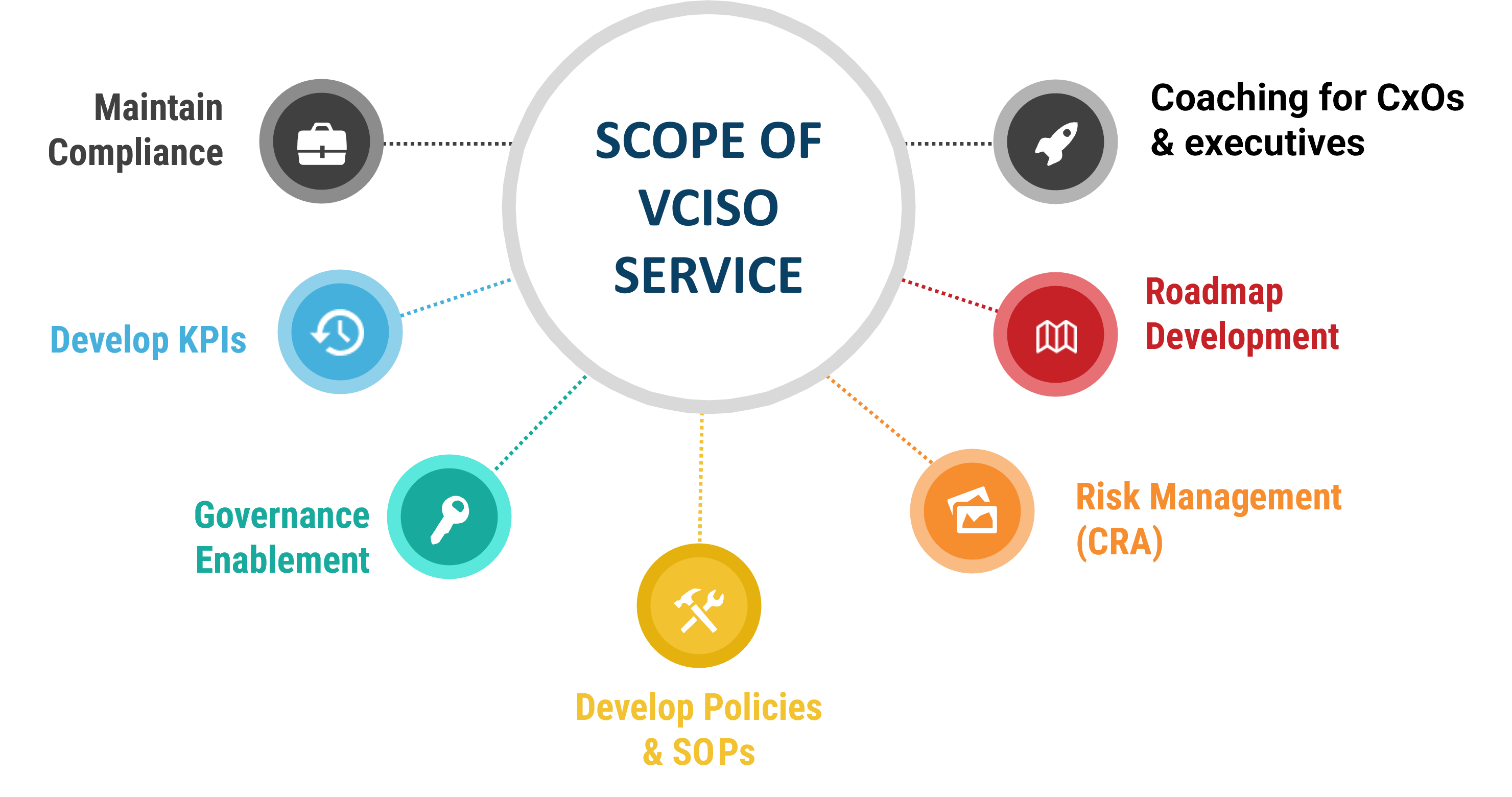
CISO as a Service (vCISO)
Securing customized and trustworthy cybersecurity expertise and guidance can be a complex undertaking with potentially high associated costs for organizations
Our vCISOs conduct comprehensive security program assessments to formulate a strategic information security program that is tightly integrated with your business goals, demonstrates measurable progress, and implements customized security protocols.
What is vCISO?
The Virtual Chief Information Security Officer (vCISO) provides flexible strategic leadership in cybersecurity. This role is responsible for developing and overseeing the implementation of security strategies, offering executive guidance without the financial commitment of a full-time position.
Our vCISO Methodology (ADIO)
Our methodology for delivering vCISO service is structured around a proven, iterative cycle developed by Cyberatos: Assess, Develop, Implement, and Optimize, or ADIO. This systematic approach guides your organization through every phase of establishing, maturing, and maintaining a robust security posture.
By continually refining controls and adapting to evolving threats and regulations, this methodology ensures not only compliance but also the sustained enhancement of your overall cybersecurity resilience.
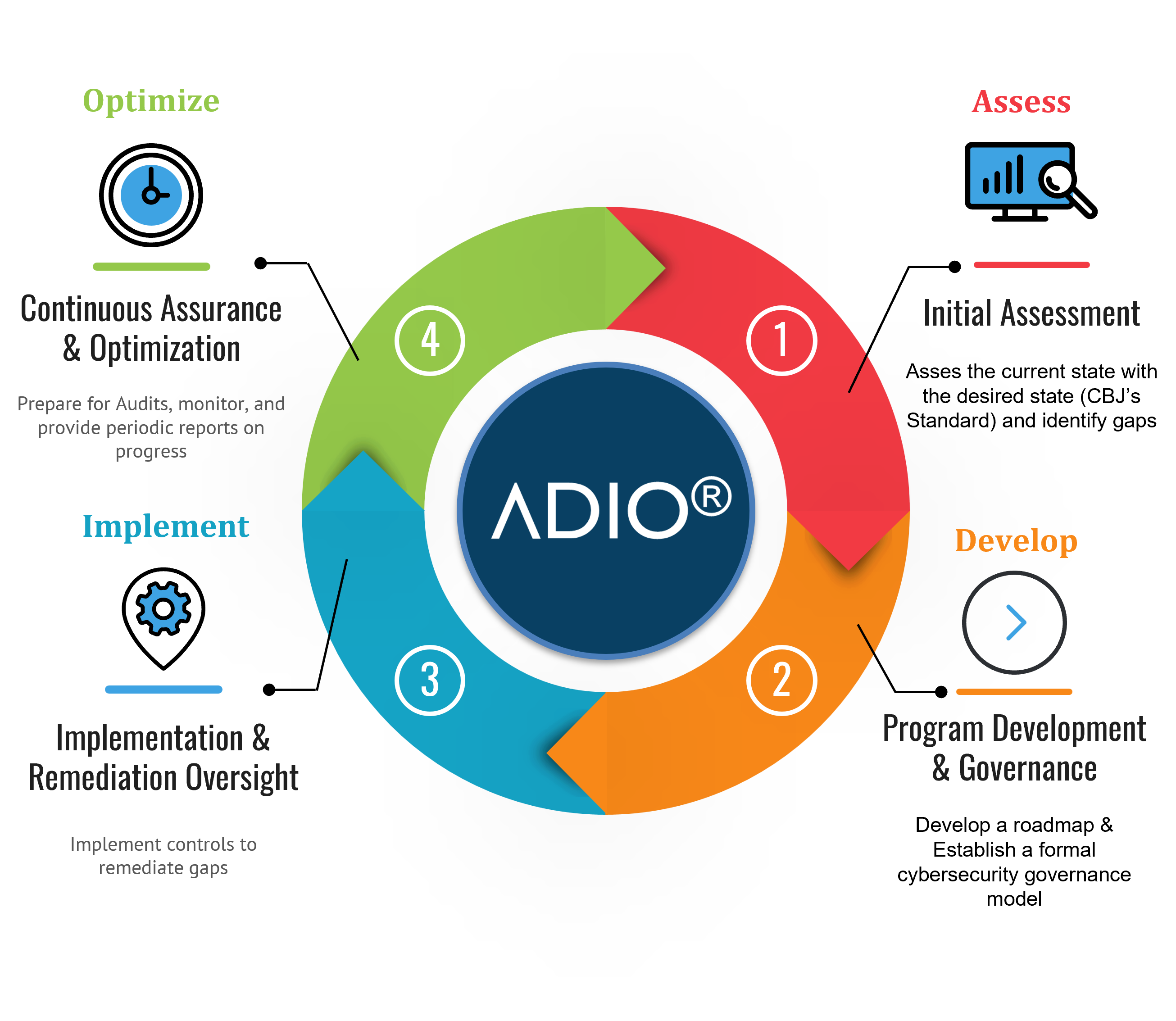

PHASE I: ASSESS
This phase is for assessment and identification. Our vCISO will assess the current posture of the client, identify assets, assess gaps, and understand the risks associated with the client's operations:
-
Understand the Landscape: Review your company's current business operations, IT infrastructure, and existing security practices, and understand processes for handling data.
-
Gap Analysis: Perform a comprehensive gap analysis, meticulously comparing your "as-is" state against the standard and regulations you're obliged to comply with.
-
Risk Appetite Definition: Work directly with your senior management and board to clearly define and gain approval for the organization's cybersecurity risk appetite. This establishes the foundational tolerance level for cyber risks, guiding all subsequent security decisions.

PHASE II: DEVELOP
Based on the assessment findings, vCISO will lead the design and documentation of the comprehensive cybersecurity strategy, policies, and management systems required by the CCG. The vCISO will:
-
Formulate Cybersecurity Strategy & Roadmap: Develop a comprehensive cybersecurity strategy and a clear implementation roadmap.
-
Establish Governance Framework: Guide the establishment of a formal cybersecurity governance model, ensuring clarity on roles, responsibilities, and reporting lines.
-
Develop Core Policies & Processes: Lead the development, approval, and communication of a comprehensive Cybersecurity Policy that aligns with your business strategy.
-
Oversight Compliance: Establish processes to continually monitor and ensure compliance with applicable cybersecurity standards and national legislations.

PHASE III: IMPLEMENT
In this crucial phase, the vCISO will guide and oversee the practical implementation of the defined strategies, policies, and controls across the insurance company. The vCISO will:
-
Operationalize Policies & Processes: Ensure the practical implementation of the developed cybersecurity policies and standards across all relevant departments and systems.
-
Prioritize & Implement Controls: Based on the gap analysis, the vCISO will prioritize remediation efforts. This will involve overseeing the deployment of a prioritized list of technical and operational controls.
-
Execute Awareness & Training: Ensure the cybersecurity awareness and training programs are regularly conducted for all specified personnel, and facilitate specialized training where recommended.

PHASE V: Optimize
The vCISO will establish mechanisms for continuous monitoring, evaluation, and optimization of the company's cybersecurity posture and compliance.
-
Audit Readiness: Prepare your organization for internal and external cybersecurity audits by ensuring all documentation is complete and controls are demonstrably effective.
-
Ongoing Monitoring & Reporting: Ensure continuous monitoring of the implemented controls and provide regular reports to leadership on security posture, risk profile, and compliance status.
-
Threat Intelligence & Information Sharing: Oversee the establishment of procedures for managing CTI, guide the use of external sources and guide information sharing.
-
Incident Response & Resilience Improvement: Ensure all incidents are reported, and that lessons learned from incidents and BCP/DR tests are incorporated into program improvements.
Benefits of vCISO

Cost-Effective Access to Top-Tier Expertise
Organizations gain access to high-level cybersecurity skills without the significant salary, benefits, and overhead costs

Enhanced Security Posture
A vCISO brings specialized knowledge to cybersecurit, leading to implementation of appropriate controls and a stronger overall security posture

Objective, External Perspective
A vCISO offers an unbiased view of the organization's security landscape, and providing fresh insights and recommendations

Alignment with Business Goals
A vCISO bridges the gap between security requirements and business objectives, driving a strategy that directly supports the growth & resilience